Picture this: A remote employee logs into their Entra ID-only laptop, expecting instant access to critical on-premises systems. Instead, they’re stuck troubleshooting a manual VPN connection, productivity stalls, and IT gets another support ticket. This is the reality for organizations using Microsoft’s AlwaysON VPN with non-domain joined or Entra ID-only devices—Microsoft doesn’t natively support automated Device Tunnel connections for these setups. I’ve built a lightweight, Windows-native solution to fix this gap, ensuring secure, seamless, and automated VPN connectivity for hybrid and cloud-first environments.
Why This Matters to businesses
The shift to cloud-first models like Microsoft Intune and Entra ID (formerly Azure AD) is transforming IT operations, enabling mobility and zero-trust architectures. However, hybrid environments remain a reality—many organizations still rely on on-premises servers for critical operations, and non-domain joined PCs are increasingly common in remote work setups. Without automation, these devices face:
- Manual VPN Connections: Employees struggle to connect, disrupting workflows.
- IT Overload: Support tickets pile up, diverting resources from strategic priorities.
- Security Risks: Inconsistent connectivity increases vulnerabilities.
- Productivity Loss: Employees waste time waiting for access to internal resources.
My solution bridges this gap, automating AlwaysON VPN Device Tunnel connections for Entra ID-only and non-domain joined Windows PCs. For decision-makers, this means reduced IT costs, improved employee satisfaction, and enhanced security. For IT teams, it’s a hands-off, scalable framework that leverages native Windows tools—no third-party software required.
Real-World Impact: A Game-Changer for Remote Work
Consider a mid-sized company with 200 remote employees using non-domain joined laptops. Without automation, IT spends hours weekly troubleshooting VPN issues, and employees lose productivity waiting for connections. After deploying our solution, VPNs auto-connect at boot, trusted networks are detected seamlessly, and logs provide IT with clear insights. The result? A secure, efficient, and frustration-free remote work experience—saving time, reducing costs, and ensuring consistent access to critical resources.
What My Solution Delivers
My PowerShell-based framework uses built-in Windows features for simplicity, reliability, and scalability. Here’s what it offers:
| Feature | Benefit |
|---|---|
| Effortless Connectivity | Auto-connects VPN at startup, user logon, and network changes—no user action needed. |
| Trusted Network Detection | Disconnects VPN on trusted networks (e.g., office LAN) to optimize performance. |
| Smart Retry Logic | Retries failed connections intelligently with up to three attempts, ensuring reliability. |
| Detailed Logging | Logs all actions in Windows Event Viewer for troubleshooting and compliance. |
| Self-Healing | Monitors connectivity every minute, maintaining persistent access without intervention. |
| Hybrid and Entra ID Ready | Supports non-domain joined and Entra ID-only PCs in cloud-on-premises setups. |
For Decision-Makers: The Business Value
- Cost Savings: Reduces IT workload by eliminating manual VPN management, freeing teams for strategic initiatives.
- Enhanced Productivity: Employees access resources instantly, boosting efficiency and satisfaction.
- Improved Security: Ensures consistent connectivity, reducing risks from user errors or missed connections.
- Cloud-First Compatibility: Aligns with Entra ID-only deployments, supporting your cloud migration strategy.
For IT Teams: The Technical Edge
- Native Tools: Uses PowerShell, VBScript, and Task Scheduler—no third-party dependencies.
- Scalable Design: Works for 10 devices or 10,000, with robust error handling.
- Security First: Runs as SYSTEM, hides scripts in a secure folder, and supports future script signing.
How It Works: A Peek Under the Hood
The solution comprises four lightweight scripts, working together to automate VPN connectivity:
- Installer (
startAndCheckVPN.bat): Deploys scripts to a hiddenC:\Scriptsdirectory and triggers task creation. - Task Scheduler (
startAndCheckVPNTasks.ps1): Sets up a Scheduled Task to run at system startup, user logon, and every minute. - Core Logic (
startAndCheckVPN.ps1): Checks network status, manages VPN connections, and logs actions. - Silent Runner (
startAndCheckVPN.vbs): Executes PowerShell invisibly, ensuring no user disruption.
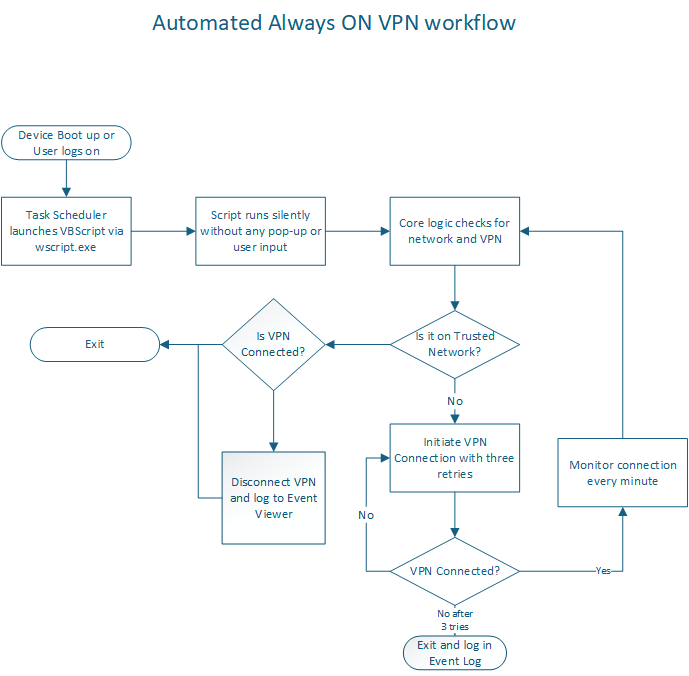
Step-by-Step Workflow
- Device Boots or User Logs On: Task Scheduler triggers the VBScript.
- Silent Execution: VBScript runs PowerShell without pop-ups.
- Network Check: PowerShell verifies if the device is on a trusted network.
- VPN Action: If not on a trusted network, it establishes the VPN with up to three retries; if on a trusted network, it disconnects the VPN if active.
- Continuous Monitoring: Re-checks connectivity every minute, looping back to network and VPN status checks.
- Logging: Records all actions (success, failure, network status) in Event Viewer under
VPNConnectionScript.
For a visual representation, check out our workflow diagram
Get Started: Deployment Made Simple
Ready to transform your remote access strategy? Here’s how to deploy our solution:
-
Prerequisites:
- Windows 10/11 with AlwaysON VPN configured.
- Administrative privileges.
- Update placeholders in
startAndCheckVPN.ps1(e.g.,$TrustedNetworkRange,$VpnName).
-
Installation:
git clone https://github.com/mukuld/automatedAlwaysONVPN.git cd automatedAlwaysONVPN .\startAndCheckVPN.bat -
Configuration:
- Edit script variables to match your environment (e.g., VPN name, network ranges).
- Verify the Scheduled Task is created (
TaskName: “Automatically connect VPN on Startup and if not connected on user logon”).
-
Test and Monitor:
- Reboot the device to confirm auto-connectivity.
- Check logs in Event Viewer (
Application>VPNConnectionScript) for insights.
For detailed instructions, visit our GitHub repository.
Security and Compliance: Built for Enterprise Needs
- SYSTEM Privileges: Runs without exposing user credentials.
- Hardened Scripts: Stored in a hidden folder (
C:\Scripts); can be code-signed for added security. - Audit-Ready: Comprehensive event logging for compliance tracking, with references to Microsoft’s PowerShell Event Logging.
Looking Ahead: Future Enhancements
We’re committed to evolving this solution to meet future needs:
- Windows Service Integration: For even tighter OS integration.
- Cross-Platform Support: Expand to macOS and Linux using native schedulers (e.g.,
launchd,cron). - Azure Monitor Telemetry: Add monitoring for enterprise-scale insights.
- Modern Authentication: Integrate Azure MFA for enhanced security.
- User Tray App: Build a simple interface for VPN status visibility.
Why Choose my solution?
- Fills a Critical Gap: Automates AlwaysON VPN for Entra ID-only and non-domain joined PCs, addressing Microsoft’s limitation.
- Drives Efficiency: Saves IT time, reduces costs, and boosts productivity.
- Scalable and Secure: Designed for hybrid environments, from small teams to global enterprises.
- Community-Driven: Open to contributions to enhance features and compatibility.
Let’s Collaborate: Join the Future of Remote Access
I am passionate about making remote work secure, seamless, and invisible to users. Ready to experience automated VPN connectivity like never before? Here’s how to get involved:
- Try It Now: Clone the repository and test it in your environment.
- Share Feedback: Have ideas to improve this solution? Email me at mukul@dharwadkar.com.
- Contribute: Join me on GitHub to file issues or contribute code: GitHub Repository.
Let’s build a future where hybrid and cloud-first work is effortless. Download our solution today and empower your workforce with reliable, secure access.
Appendix
Script List:
startAndCheckVPN.batstartAndCheckVPN.ps1startAndCheckVPN.vbsstartAndCheckVPNTasks.ps1
References:
Copyright © 2025 Mukul Dharwadkar. All rights reserved.

